Tech & Security
From iPhone to Institutional Wallets: Why Security by Design Is the Only Way Forward
When Apple unveiled its new iPhone 17 and iPhone Air lineup, most of the buzz was about the usual upgrades. But the most groundbreaking new feature isn't visible at all—it's an invisible shield called Memory Integrity Enforcement (MIE), and it’s one of the most significant architectural upgrades in the history of consumer operating systems. By making memory safety checks always-on, Apple has raised the bar against entire classes of exploits such as buffer overflows and “use after free” vulnerabilities.
For billions of iPhone and Mac users, this advancement is invisible yet fundamental. Security isn’t something you “turn on.” It’s built into the hardware, the operating system, and the user experience.
This follows on from our earlier coverage of Apple Exclaves, where secure enclaves contribute technically to enforcing these protections. This article will explain what MIE is, the dangerous digital problem it solves, and why Apple calls it "the most significant upgrade to memory safety in the history of consumer operating systems."

Security by Design: Apple’s Approach
Apple’s MIE combines hardware and software defenses to protect critical processes. It leverages enhanced memory tagging, secure allocators, and tag confidentiality to detect and prevent attacks at runtime, without developers or users needing to intervene.
The philosophy is clear: security must be enforced by default. Not optional. Not a trade-off.
1. The Problem: A Tiny Digital Flaw With Costly Consequences
To understand Apple's new shield, we first need to understand the threat it was designed to stop. The danger lies in tiny, common coding mistakes called "memory bugs."
What is a Memory Bug?
Think of your iPhone's memory (RAM) as a massive, high tech hotel. When you open an app, the system assigns it a "room" (a block of memory) to temporarily store its data – like your progress in a game or the text you're typing. Everything is supposed to stay neatly within its own room.
A memory bug is a flaw in an app's code that allows it to access memory outside of its assigned room. This is like a hotel guest accidentally getting a key that can open other guests' rooms, leading to chaos and security breaches.
The Two Hacks MIE is Designed to Stop
MIE is specifically designed to stop two of the most common and dangerous types of memory bugs, which have been exploited by hackers for decades.
1. Buffer Overflows: This is like an app's data "spilling over" from its hotel room into the hallway or the next room. Imagine trying to cram too much luggage into a small room; eventually, it bursts through the door. In the digital world, this overflowing data can corrupt or overwrite the data of other apps, causing crashes or, worse, giving an attacker an opening to run malicious code.
2. Use-After-Free: This happens when an app tries to use its keycard on a room after it has already checked out. The hotel management (the operating system) has already cleaned the room and given it to a new guest (another piece of data). When the first app tries to use its old key, it ends up in the wrong room, accessing data it shouldn't and creating a major security risk.
Why You Should Care
These seemingly small bugs are the primary tools used by developers of sophisticated "mercenary spyware," like the infamous Pegasus. These groups build multi-million-dollar hacking tools that chain these memory bugs together to break into the phones of high-value targets like journalists, activists, and political dissidents. By exploiting a buffer overflow in one app and a use-after-free bug in another, they can silently take complete control of a device.
The fact that these exploit chains cost millions of dollars highlights just how serious—and valuable to attackers—these tiny flaws are. This is the problem Apple set out to solve: not just patching individual bugs as they are discovered, but eliminating entire categories of attacks before they can even start.
2. The Solution: How Your iPhone's New "Digital Bouncer" Works
Instead of just trying to build stronger walls for each hotel room, Apple's solution puts a hyper-aware security guard at every single door.
Meet Memory Integrity Enforcement (MIE)
Memory Integrity Enforcement (MIE) is Apple's powerful new security system, built directly into the iPhone's A19 chip. It acts as a tireless "digital bouncer" for your phone's memory.
Here’s how it works, using our hotel analogy:
• A Bouncer at Every Door: The iPhone's hardware (the A19 chip) acts as a new security bouncer stationed at every single memory "room."
• Unique, Secret Keys: When an app is assigned a piece of memory (a room), it's also given a unique, secret digital key. This is called an EMTE "tag."
• Constant, Instant Checks: Every single time the app tries to access its memory—whether to read data or write new data—the hardware bouncer instantly checks if the app's key matches the room's lock.
• Immediate Crash: If the key is wrong, even slightly, the bouncer doesn't just block access. It instantly crashes the app to stop any potential attack before it can cause harm. This transforms a subtle memory bug that a hacker could exploit into a harmless app crash, which is exactly the desired outcome.
While this system is incredibly powerful, the secret keys have a small number of possible values (a 4-bit tag), meaning there's still a slim, 1-in-16 chance an attacker could get lucky. However, this dramatically reduces the reliability of an attack, often from a guarantee to a gamble.
The Three Pillars of MIE
This system is built on three core components that work together to create a comprehensive defense.
• Smart Room Assignments The system intelligently organizes different types of data, much like a hotel manager putting business guests and vacationing families on separate floors to prevent mix-ups. This is done by "secure memory allocators," which make it harder for an old key from one type of room to accidentally work on another.
• Instant Key Checks The security check happens instantly and continuously ("synchronously") for every single memory access. This is a crucial detail; other modes can check asynchronously, which "doesn’t immediately raise an exception, leaving a race window open for attackers." MIE's synchronous check closes this race window, leaving no opportunity for an attacker to slip through.
• Un-copyable Keys The secret keys ("tags") are protected from being copied or spied on by attackers using other clever tricks, like "side-channel attacks." This feature, called Tag Confidentiality Enforcement, ensures the bouncer's security system can't be compromised.
By combining these hardware and software defenses, MIE creates a system that doesn't just react to threats but fundamentally changes the rules of the game for attackers.
3. Why This is a Game-Changer for iPhone Security
MIE's real power isn't just in stopping a single bug; it's about making the entire process of hacking a device exponentially harder and more expensive.
Breaking the Exploit Chain
Hackers rarely break into a device with a single trick. They use a set of exploits, linking multiple small vulnerabilities together like dominoes to gain progressively more control. An attack might start with a bug in a messaging app, then use another bug in the web browser, and a final one in the core operating system to take over the phone.
MIE's primary benefit is breaking a critical link in this chain. If an attacker's first step relies on a memory bug, MIE stops it cold. The entire attack fails before it can even get started.
A Deeper Defense Than Lockdown Mode
It’s important to understand how MIE differs from Apple’s other major anti-spyware tool, Lockdown Mode. These two features solve the problem in fundamentally different ways. Lockdown Mode protects you by drastically reducing the attack surface—it disables entire features, like iMessage link previews, so the vulnerable code never has a chance to run. In contrast, MIE protects you by hardening the underlying exploit mechanism. It allows features to run as normal but stops the memory bug from being weaponized, turning a potential hack into a safe app crash.
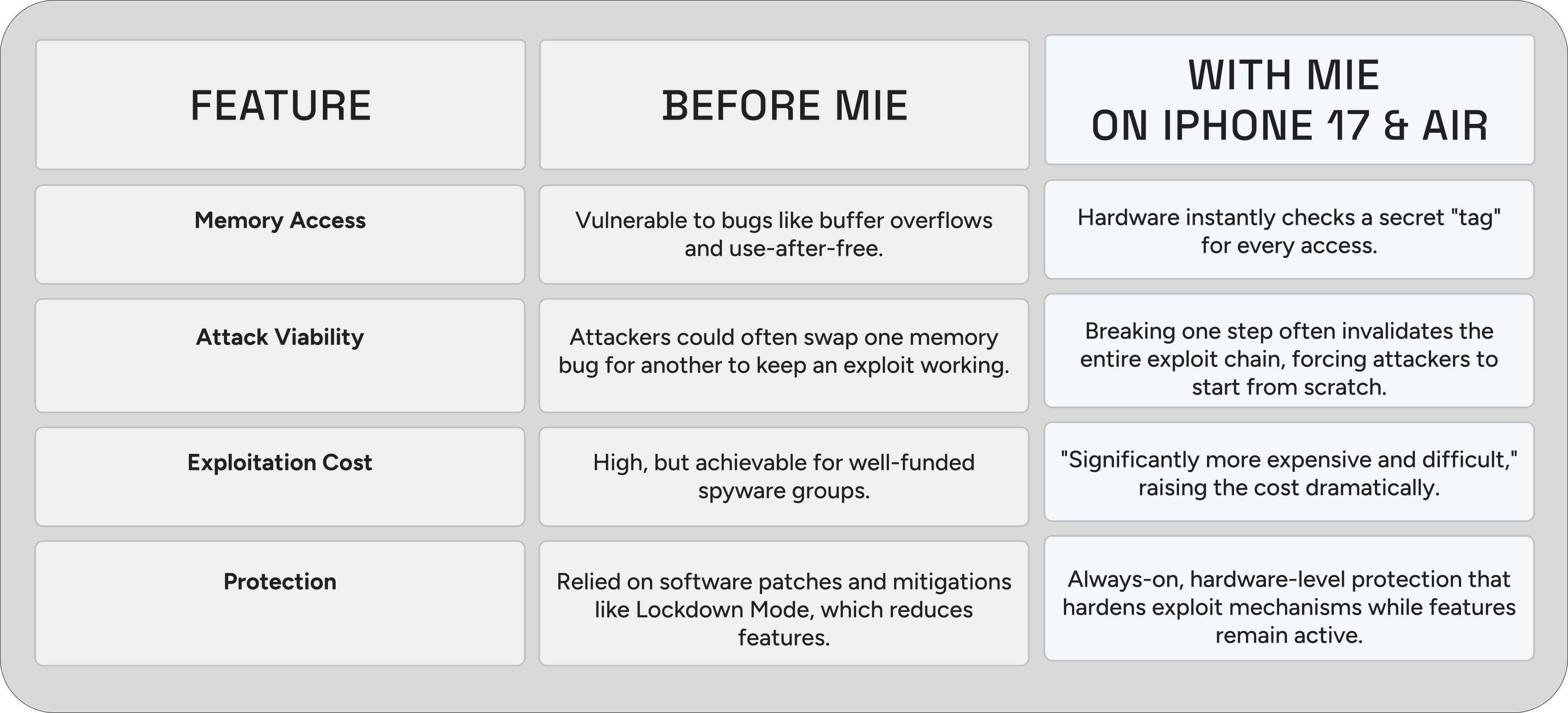
Before MIE vs. With MIE
This table shows how dramatically the security landscape changes with MIE on the new iPhone 17 and iPhone Air.
The 3 Biggest Benefits for You
Even if you're not a high-profile target, this new security foundation provides significant benefits.
1. Making Spyware Too Expensive to Work MIE raises the cost and difficulty for attackers so high that it may deter them from even trying. When a multi-million dollar attack can be stopped by a single, fundamental hardware check, the economics of spyware development begin to collapse.
2. Protection You Don't Have to Think About This isn't a setting you have to turn on. MIE is on by default. According to Apple, MIE is so deeply integrated into the A19 chip that it runs invisibly in the background with negligible impact on performance or battery life. It protects you automatically, all the time.
3. A Stronger Foundation for Everyone While MIE's primary target is sophisticated spyware, this fundamental security upgrade makes the entire iPhone platform more resilient. By eliminating entire classes of vulnerabilities, Apple is building a stronger, safer foundation that protects all users against all types of future threats.
Ultimately, MIE represents a powerful new layer of defense that makes every user safer.
4. Conclusion: A Safer Digital Life by Design
Memory Integrity Enforcement represents a major shift in security philosophy—moving from reacting to individual bugs to proactively preventing entire classes of attacks at the hardware level. It's a defense that is always on, deeply integrated, and designed to disrupt the very economics of the spyware industry. While no technology is perfectly secure, MIE makes the iPhone a dramatically harder target for even the most advanced hackers, and that is a significant victory for user privacy and security everywhere.
What about Android?
The Android ecosystem relies on the foundational Memory Tagging Extension (MTE), an ARM specification released in 2019, which Google began implementing in devices like the Pixel 8. A key distinction lies in the operational modes: MTE supports both Synchronous (SYNC) and Asynchronous (ASYNC) modes.
While Apple employs synchronous checking exclusively for MIE, Android implementations, often balancing performance with security, frequently utilize the less precise ASYNC mode in production due to its low overhead (estimated at 1-2%), despite the drawback that ASYNC leaves a vulnerability race window open for attackers. To boost protection, Google does offer its stricter Advanced Protection mode for Pixel users. The custom operating system GrapheneOS has significantly advanced MTE adoption, deploying it shortly after the Pixel 8 launch.
Importantly, GrapheneOS offers users a simple toggle to enable this hardware memory tagging for all installed third-party applications, addressing memory safety risks in frequently targeted apps like Signal and WhatsApp
Furthermore, Android implements other hardware-level protections, such as ShadowCallStack (SCS), which is crucial for Control flow integrity (CFI), an essential component of the system's exploit mitigation layer.
The io.finnet Parallel
Managing institutional digital assets faces similar challenges. Attack surfaces are vast, exploits evolve quickly, and the cost of failure is immense.
At io.finnet, we apply the same principle — uncompromising security by design — but extend it to the way institutions actually work:
- Trustless MPC: No single point of failure, no dependency on a provider co-signer.
- Virtual Signer: Automate transactions with flexible policies and rules, without lowering defenses.
- Mobile Signing (iPhone & Android): Teams can securely authorize transactions straight from their phone, with the same level of protection as desktop.
- Passkeys: Seamless, device-native authentication for intuitive and secure access.
This means the highest level of institutional security doesn’t come at the cost of agility or accessibility. Teams can act quickly — from their iPhone, Android, or automated workflows — while remaining fully protected.
Why It Matters
Whether it’s your iPhone in your pocket or a vault managing billions in digital assets, the principle is the same:
Security isn’t an add-on. It’s enforced by design — and it must remain accessible.
Apple’s MIE shows the direction consumer technology is heading. io.finnet brings the same philosophy to institutional finance — delivering uncompromising protection that works seamlessly across mobile, desktop, and automation.
Learn more
Explore how io.finnet makes institutional self-custody both secure and accessible: iofinnet.com, io.finnetGitHub, API documentation and technical guides
We are also planning to enable EIP protections in our app, bringing the same always-on memory safety principles to digital asset infrastructure.


.svg)